Insights & Research for Smarter Business
Expert Analysis. Market Trends. Future Strategies.
Stay ahead with expert insights on eCommerce research, digital transformation, and AI-led business models. Explore data-backed strategies and innovation frameworks designed for startups, enterprises, and future-ready businesses across industries.
Schedule a Phone or Zoom Call
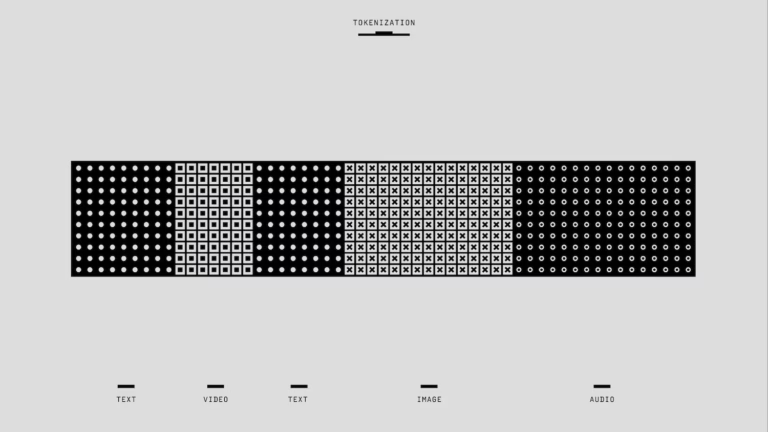
TokenOps: Optimizing Token Usage in LLM API Applications via Pre- and Post-Processing Layers
The adoption of Large Language Models (LLMs) such as GPT-4 and Claude 3 has introduced significant operational challenges, primarily associated with escalating costs, latency, and computational load resulting from excessive token usage. Tokens, beyond mere computational units, represent direct economic and environmental costs. This research presents the TokenOps framework, a…
Emerging Consumer Trends: How Value-Oriented Buying is Reshaping India’s Market Landscape – Chitrangana Byte
In a bustling market, Indian consumers are undergoing a significant shift in purchasing behavior. Gone are the days of brand loyalty driven solely by familiarity; today, value and quality reign…
Live Commerce: A Game Changer for India’s E-commerce Landscape | Chitrangana Analysis
Picture this: a middle-class family in India, gathered around their television, captivated by a live shopping show. This scene, once a staple of weekend entertainment, is making a comeback in…
TokenOps: Optimizing Token Usage in LLM API Applications via Pre- and Post-Processing Layers
Posted on April 24, 2025
The adoption of Large Language Models (LLMs) such as GPT-4 and Claude 3 has introduced significant operational challenges, primarily associated with escalating costs, latency, and computational load resulting from excessive token usage. Tokens, beyond mere
Ambient Commerce: India’s Leap from Screen to Scene in AI-Driven Retail
Posted on April 22, 2025
The Signal Shift: From Touchscreens to Talkback In 2025, India’s fastest-growing retail interfaces are no longer screens. They’re smart speakers, mirrors, cars, and fridges. Voice commerce and ambient AI are laying the groundwork for a
The Backend Battleground: Why D2C Growth Now Belongs to Operations, Not Marketing
Posted on April 20, 2025
The Situation: D2C’s Frontend Boom Is Hitting a Backend Wall Over the past decade, Direct-to-Consumer (D2C) brands have surged by capitalizing on a direct line to their customers, powered by performance marketing, social storytelling, and
The 2025 Digital Workshift: Agentic AI and the End of Top-Down Leadership
Posted on April 19, 2025
In 2024, organizations across sectors faced an unprecedented crossroads. Global economic turbulence, rapid technological advancements, and heightened geopolitical tensions collectively forced business leaders to question deeply ingrained operational assumptions. Executives confronted difficult decisions: prioritizing rapid
India’s Untapped Mental Health Market: A Human-AI Wellness Concept That’s Ready to Lead Change
Posted on April 17, 2025
What happens when 40% of the population quietly suffers from mental health challenges, but less than a third receive help? In India, that’s not a hypothetical—it’s the daily reality. Despite rising awareness, access to qualified
AI Integration in Indian Education: Why the Future Needs a New Beginning
Posted on April 16, 2025
“We know AI matters, but we don’t know where to start.” This single sentence echoes across countless boardrooms and classrooms in India today. From school administrators in tier-2 towns to the deans of prestigious universities,
The Instant Delivery Tipping Point: How Indian Shoppers Are Reshaping Retail for 2025
Posted on April 15, 2025
What if 28% of your customers expected their orders within an hour? That’s not a hypothetical—it’s a forecast for Indian e-commerce by 2025. With rising digital adoption and lifestyle shifts, Indian consumers are placing a
Unlocking a Game-Changing Startup Opportunity: Personalized Ayurveda in eCommerce
Posted on November 19, 2024
Ayurveda, the ancient Indian system of wellness, is stepping into the future with innovation. As the global demand for personalized and natural wellness solutions skyrockets, integrating Ayurveda with technology and…
भारत की आर्थिक मंदी 2024-25: विकास के ड्राइवर्स और नीतियों में खामियां
Posted on November 15, 2024
भारत की आर्थिक मंदी: विकास के ड्राइवर्स और नीतियों में खामियां भारत, जिसे दुनिया की सबसे तेजी से बढ़ती अर्थव्यवस्थाओं में से एक माना जाता है, अब एक मंदी का…
India’s Economic Slowdown (2024-2025): An In-Depth Analysis of the Growth Drivers and Policy Gaps
Posted on November 15, 2024
India’s Economic Slowdown: An In-Depth Analysis of the Growth Drivers and Policy Gaps India, often hailed as one of the world’s fastest-growing economies, is facing a slowdown that has sparked…
Lab-Grown Diamonds: The Future of E-Commerce and Sustainable Luxury
Posted on November 15, 2024
At Chitrangana, India’s leading eCommerce consultancy with over 20 years of experience in the online jewelry market, we’ve witnessed firsthand the transformation of consumer behavior in luxury retail. Our deep…
The Future of Real Estate in India: Using eCommerce to Fight Black Money
Posted on September 10, 2024
For years, the real estate market in India has been known for dealing with black money—unreported cash transactions that happen under the radar. Despite efforts from the government, such as…
The Rise of D2C Brands : Is the Party Over for E-commerce Giants in India?
Posted on April 9, 2024
This article explores a fascinating shift in the Indian e-commerce landscape: the growing popularity of direct-to-consumer (D2C) brands and the potential decline of major marketplaces. Our research at Chitrangana.com indicates…
AI in the Fast Food Industry: A Futuristic Approach
Posted on April 7, 2024
By Principal Business Advisor, Chitrangana.com – The Leading eCommerce Consultancy of India. The fast food industry is on the brink of a technological revolution, and it’s time for businesses to…
E-commerce Trends 2024-2027: A Data-Driven Analysis by Chitrangana.com
Posted on April 4, 2024
In this report, we delve into the significant shifts and growth projections within the e-commerce industry, providing a detailed, data-centric overview to guide businesses in their strategic planning. Online Retail’s…